1. Pre-requisites:
1. Ensure that the user account used for creating the storage account has access to join the storage account to the domain and has Owner access on the Azure Portal to facilitate resource creation. After deployment, this role can be revoked.
2. Go to Subscriptions -> Resource Providers. Search for 'Storage.' For Microsoft.Storage, click on the three horizontal dots and select 'Register.' It will then show as registered.

3. A computer joined to your domain is used for installing and running PowerShell modules to join a storage account to your domain. Typically, a Server VM is used for this purpose.
4. The VNet used by the Server VM should have internet access, as PowerShell will need to download the modules required for joining the storage account to the domain.
5. An Organizational Unit (OU) for the Storage Account computer object.
2. Cost Consideration:
Premium file shares have a fixed billing model where you pay for the storage capacity you choose, regardless of actual usage. Standard file shares use a pay-as-you-go model, where you pay based on how much storage you use and the number of transactions.
3. Best Practices:
1. The storage account should be in the same region as your host pool session hosts to minimize latency.
2. During the Storage Account creation process, select Premium in the Performance tier for fast performance and low latency.
3. Select Zone Redundant Storage (ZRS) for redundancy. If the region has three datacenters, your storage account data will be replicated across all of them. This ensures that even if one datacenter fails, your data will still be available in the remaining datacenters
If you choose Locally Redundant Storage (LRS), your data is stored across multiple racks within the same datacenter. In the event of a datacenter failure, you could lose access to your data.
4. For Encryption type, select Microsoft-managed keys as they are suitable and offer convenience with minimal management overhead. However, if you need advanced control and compliance requirements, customer-managed keys are the better choice. Microsoft manages the appropriate rotation of Microsoft-managed keys per compliance requirements. If it is Customer Managed key, customer has to manage the rotations.
5. Create two separate containers: one for Profile Share and one for ODFC Share. The reason is that the ODFC container will only contain cache data for MS Teams, Outlook, and OneDrive. Even if you delete the ODFC share, Azure will automatically download all the cache data from the cloud. Additionally, there is no need to configure backups for the cached data.
6. Instead of granting access to each user individually, create a security group in Active Directory, add all the users to this group, and then grant access to the security group.
7. Create a dedicated subnet in the Hub Vnet for the private endpoints. If in case Azure WAN is being used in the environment, create a dedicated subnet in the Spoke Vnet for the private endpoints.
8. Use Static IP allocation for private endpoints if you need a stable and predictable IP address for consistent network management and security.
9. Implement and make use of Azure Private DNS zones for DNS resolution, ensuring that service names resolve correctly to the Private Endpoint's private IP address.
4. Creation of Azure Storage Account:
1. In the Global Search, search for Storage accounts in the search bar. Select + Create.
2. Select the required Subscription and the Resource Group.
3. Enter a unique name for your storage account. This name must be unique globally and cannot contain any capital letters.
Note: Additionally, if the storage account is going to be joined to the Active Directory domain, the name of the storage account should be a maximum of 15 characters, as the computer object created for the storage account can only have up to 15 characters
4. Select the Region. Do not click "Deploy to an Azure Extended Zone" as it is currently in PREVIEW. It only supports premium storage accounts with locally-redundant storage (LRS) redundancy which does not suit the AVD purpose.
5. Select the Performance as Premium.
6. Premium Account type as File Shares. This option is suitable since we will use this storage account to store user profiles.
7. Redundancy as Zone-redundant storage.
8. Click Next.
9. In the Advanced tab, select Require secure transfer for REST API operations. Uncheck other options if selected.
10. For Permitted Scope for copy operations select From Storage Accounts that have a Private Endpoint to the same Virtual Network.
11. Leave the Hierarchical Namespace, Access protocols and Blob storage options as it is not for Azure File Share.
12. Click Next.
13. Leave the Networking tab for now. We will disable Public access and enable Private access at a later stage. Click Next.
14. In the Data Protection tab, select 'Enable soft delete' for file shares. The default retention period is 7 days, but you can specify any number of days depending on the customer's requirements. This is the only required and applicable option for file shares. Soft delete protects your data from accidental deletion by retaining the deleted data in the system for a specified period.
15. Click Next.
16. In the Encryption tab, for encryption type select Microsoft-managed keys.
17. Check the box for enable infrastructure encryption.
18. Click Next.
19. Give the Tags, click Next. Click on Create.
5. Creation of Azure File Share:
1. Search for the Storage account created, click on the Storage account, in the data storage dropdown select File Shares. Click on + File Share.
2. In the basics tab, give a name for the share.
3. Minimum provisioned capacity is 100 GB.
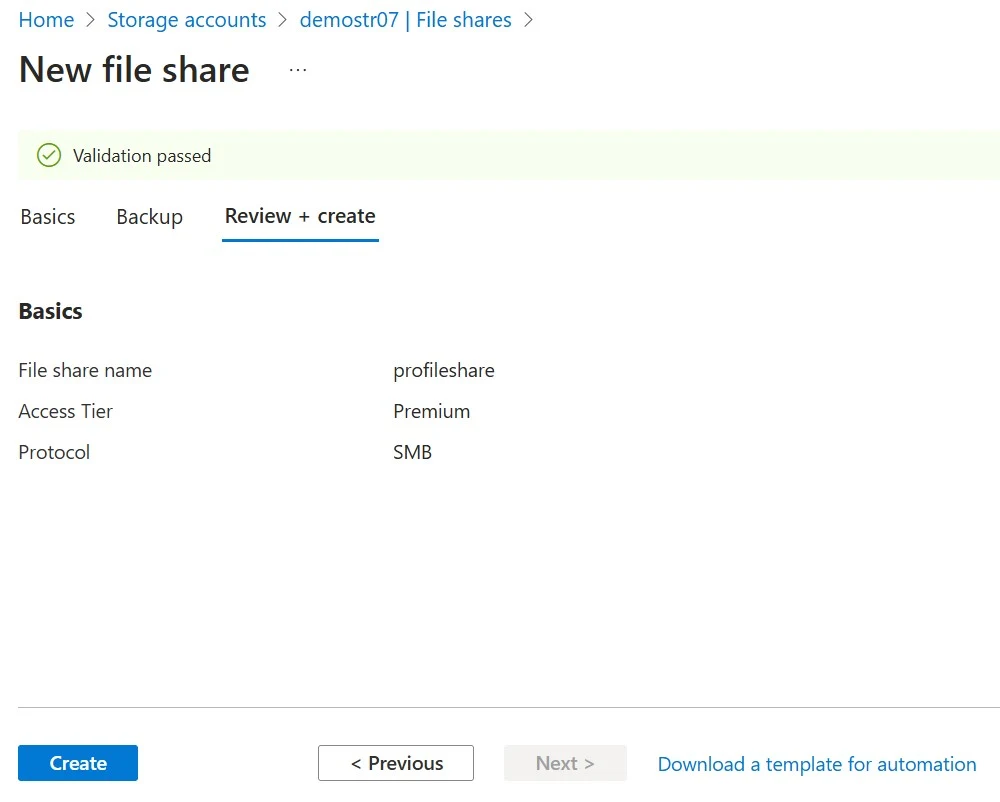
4. For Protocol, select SMB. Click Next-Backup.
5. For now uncheck the Backup option, we will configure the Backup in the upcoming Blog. Click Review +create.
6. Click on Create.
7. Similarly, create a file share for ODFC share as shown:
6. Join the storage account to Active Directory:
1. Sign in to a computer that is joined to your domain.
Click on the AzFilesHybrid.zip file and extract it. Make a note of the folder where you extract the files. This step is necessary to download the Az Modules into PowerShell, as we will need them.
3. Open an elevated PowerShell prompt
4. Run the below command to unblock importing AzFilesHybrid.psm1 module
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope CurrentUser
Say Yes to All when you receive a prompt.
5. Change to the directory where you extracted the files.
6. Type .\CopyToPSPath.ps1 in the PowerShell window.
Click on Run Once when you receive a prompt.
7. Run Import-Module -Name AzFilesHybrid in the PowerShell window.
Select Run Once and Yes to All when you receive the prompts.
8. At this point, close the PowerShell window and open it again using 'Run as Administrator.
9. Repeat steps 4 to 7.
10. It may take a couple of minutes to download all the required Az modules.
Once the process is completed, you may see a below screen. You can ignore the warning.
11. Run Connect-AzAccount in PowerShell.
You may come across below error.
12. In that case, run Update-AzConfig -EnableLoginByWam $false
13. Run Connect-AzAccount in PowerShell.
A browser will open up automatically for you to enter the username and password for your Azure Subscription.
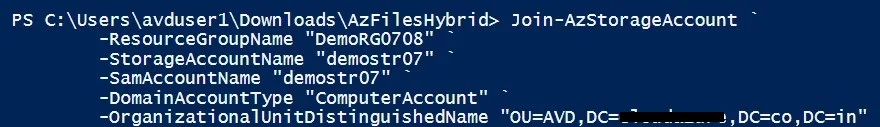
14. Register the storage account with your Active Directory Domain under the target OU.
Run the below commands:
Join-AzStorageAccount `
-ResourceGroupName $ResourceGroupName `
-StorageAccountName $StorageAccountName `
-SamAccountName $SamAccountName `
-DomainAccountType $DomainAccountType `
-OrganizationalUnitDistinguishedName $OuDistinguishedName
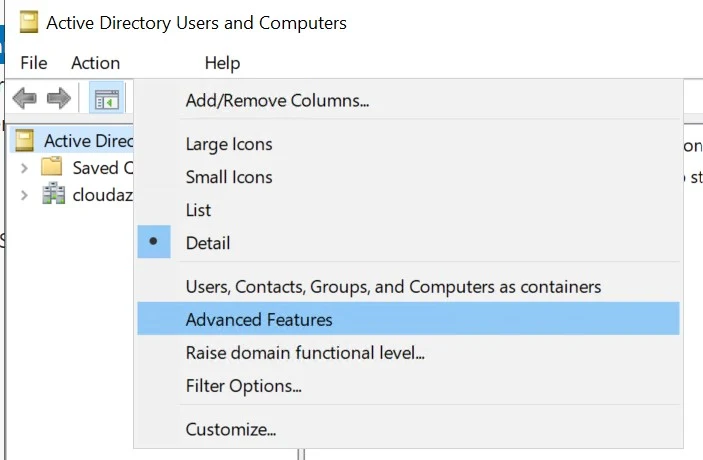
- To know the Distinguised Name or the complete path of the OU, go to your AD Domain->Server Manager->Tools->Active Directory User and Computers
- Click on View->Advanced Features
- Right Click on the desired OU. Then Properties.
- Click on Attribute Editor. Copy Paste the name you see in the distinguishedName tab.
15. Go back to Step 14, fill in the details and run the command in the PowerShell as shown:
16. You can check in the OU, the computer object for the storage account should be created.
17. If you do not have access to the AD console, run the commands below in the same PowerShell screen and review the output, replacing the values for $resourceGroupName and $storageAccountName with your values:
(Get-AzStorageAccount -ResourceGroupName $resourceGroupName -Name $storageAccountName).AzureFilesIdentityBasedAuth.DirectoryServiceOptions; (Get-AzStorageAccount -ResourceGroupName $resourceGroupName -Name $storageAccountName).AzureFilesIdentityBasedAuth.ActiveDirectoryProperties

7. Assigning RBAC role to users on the Azure Portal.
1. For the Users to create and store profiles in both the profile and ODFC share, they will need permission to access it. To do this, you'll need to assign the security group the Storage File Data SMB Share Contributor role.
From the Azure portal, browse to the storage account, then to both the shares you created previously.
Select Access control (IAM).
Select + Add, then select Add role assignment from the drop-down menu.
2. Select the role Storage File Data SMB Share Contributor and select Next.
3. On the Members tab, select User, group, or service principal, then select +Select members. In the search bar, search for and select the security group that contains the users who will use Profile Container.
4. Review and Assign.
5. Follow the same step and assign the RBAC role to the ODFC container as well.
6. Now, you need to assign the role 'Storage File Data SMB Share Elevated Contributor' to the user account you used to create the storage account and join it to the domain.
7. From the Azure portal, browse to the storage account,
Select Access control (IAM).
Select + Add, then select Add role assignment from the drop-down menu.
8. Select the role Storage File Data SMB Share Elevated Contributor and select Next.
9. On the Members tab, select User, group, or service principal, then select +Select members. In the search bar, search for and select the user account.
10. Review and Assign.
8. Set NTFS permissions on the share.
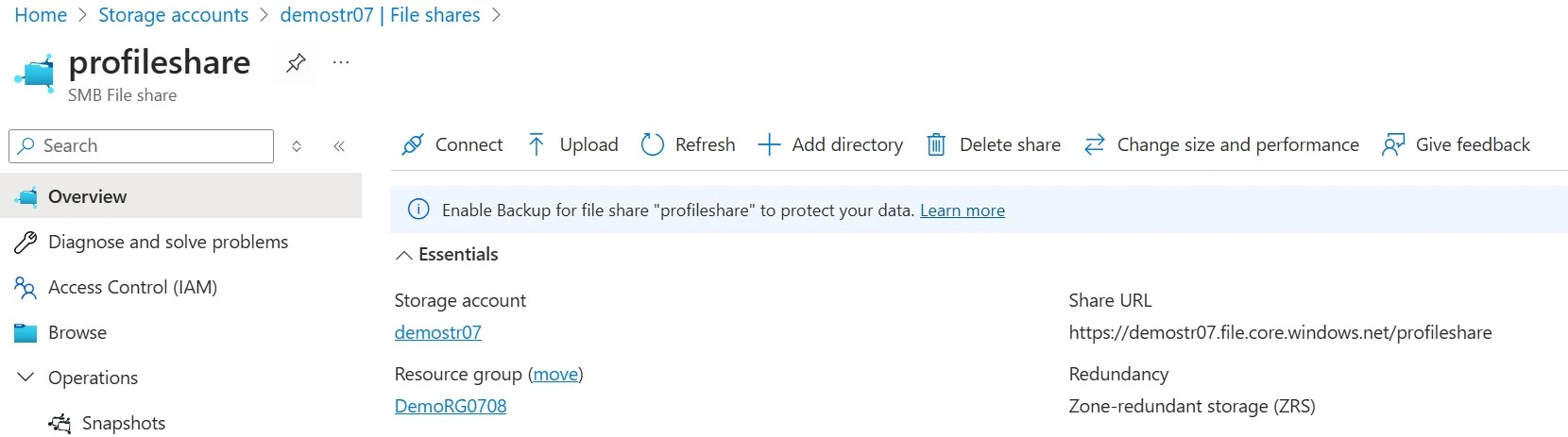
1. Copy the UNC path https://demostr07.file.core.windows.net/profileshare from the Storage Account.
2. Change it to \\demostr07.file.core.windows.net\profileshare and open in it in the File Explorer.
3. You may encounter the below error:
4. In this case, run the command below in PowerShell. This command will help us determine if Port 445, which is required for the SMB share, is open.
$resourceGroupName = "<your-resource-group-name>"
$storageAccountName = "<your-storage-account-name>"
# This command requires you to be logged into your Azure account and set the subscription your storage account is under, run:
# Connect-AzAccount -SubscriptionId 'xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx'
# if you haven't already logged in.
$storageAccount = Get-AzStorageAccount -ResourceGroupName $resourceGroupName -Name $storageAccountName
# The ComputerName, or host, is <storage-account>.file.core.windows.net for Azure Public Regions.
# $storageAccount.Context.FileEndpoint is used because non-Public Azure regions, such as sovereign clouds
# or Azure Stack deployments, will have different hosts for Azure file shares (and other storage resources).
Test-NetConnection -ComputerName ([System.Uri]::new($storageAccount.Context.FileEndPoint).Host) -Port 445

5. This means, Port 445 is not opened, which is causing the issue. You may connect with your security team and have this opened up for the time being. Once the NTFS permissions are added on the share and Private Endpoint is configured for the storage account, this port can be blocked.
6. You can go to the Azure Firewall, create a Network Rule as shown below:
7. Once the rule is set, run the above PowerShell command again:
8. TCP test shows as succeeded.
9. Copy \\demostr07.file.core.windows.net\profileshare and open in it in the File Explorer. Right Click and Click on Properties.
10. Click on Security->Advanced. Click on Disable Inheritance.
11. Modify access for Creator Owner on Subfolders and file only.
Full Control for Domain Admins/Administrator Group on this folder, subfolders and files.
Modify access for the security group on this folder only.
12. The final permission should look like this:
13. Copy the path for ODFC container \\demostr07.file.core.windows.net\odfcshare in the similar way from the Azure Portal and open in it in the File Explorer and perform Steps 9 to 11.
14. In this way, NTFS permissions have been applied to the Profile Share and ODFC Share.
9. Create Private Endpoint for the Storage account.
1. Select the Storage Account. In Security + networking, select Networking. Under Networking, select Private Endpoint connections and click on Private Endpoint.
2. In the Basics tab of Create a private endpoint, select the subscription, resource group. Give a name to the private endpoint instance. The network interface name gets auto populated. Select the Region. Click on Next.
3. In the Resource pane, subscription, resource type and resource get auto populated. In the target sub-resource select file. Click Next.
4. Select the Virtual Network and the Subnet.
Go with Statically allocate IP address.
Give the Name and Private IP address against each Member name. These IP address should be from the Subnet you provided.
Click Next.
5. Select Yes to Integrate with Private DNS Zone. Click Next.
6. Give the Tags. Click Review +Create.
7. Search for the Private Endpoint in the Global search, select the Private Endpoint we just created. You can see the Private IP assigned to the Storage Account.
8. To confirm if the Storage account is resolving to the Private IP of its Private endpoint, run the below command: nslookup demostr07.file.core.windows.net.
9. Now, disable Public Access for the Storage Account. In the global search, enter Storage account. Select the storage account we created. In Security + networking, select Networking. Under Firewall and Virtual Networks tab, Select Disabled. Click on Save.
10. This completes the process of creating the Private Endpoint for the Storage Account.






















































Comments
Post a Comment